A data breach occurs when personal information is accessed or disclosed without authorisation or is lost. A breach may happen due to a malicious or criminal attack such as a cybercrime, through human error, or a system fault.
The Notifiable Data Breaches (NDB) scheme was established in February 2018 to better protect consumers and their personal information. Under the scheme, any organisation or government agency covered by the Privacy Act 1988 must notify:
- Individuals affected by a data breach.
- The Office of the Australian Information Commissioner (OAIC), when a data breach is likely to result in serious harm to an individual whose personal information is involved.
The OAIC publishes twice-yearly reports on notifications received under the NDB scheme to track the leading sources of data breaches and highlight key issues for regulated entities to be aware of.
This article explores the findings from the OAIC report covering notifications made under the NDB scheme from July to December 2022.
Key findings
497 breaches were notified under the scheme from July to December 2022, an increase of 26% compared to 393 breaches notified in January to June 2022.
Key findings include:
- There was a 41% increase in data breaches resulting from malicious or criminal attacks. Malicious or criminal attacks accounted for 350 notifications – 70% of all notifications.
- Human error was the cause of 123 notifications (25% of all notifications), down 5% in number from 129.
- Of all sectors, health reported the most breaches (71), followed by finance (68).
- Contact information remains the most common type of personal information involved in breaches.
- The majority (88%) of breaches affected 5,000 individuals or fewer.
- 71% of entities notified the OAIC within 30 days of becoming aware of an incident.
Malicious or criminal attack breaches
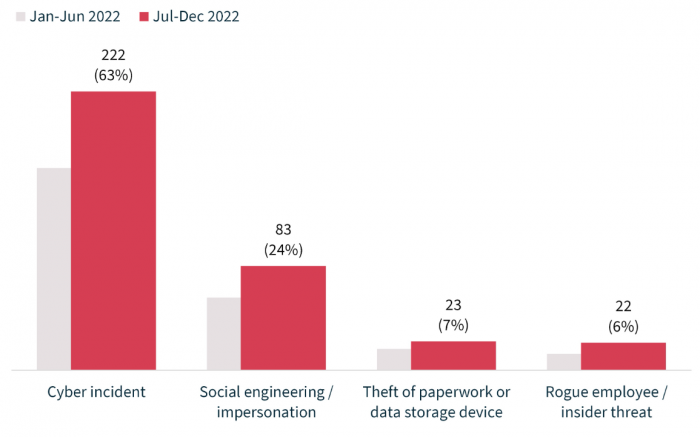
The majority (63%) of breaches caused by malicious or criminal attacks were cyber incidents. There were 222 breaches resulting from cyber incidents, up 38% from 161 in the previous reporting period.
Social engineering or impersonation accounted for 24% of data breaches caused by malicious or criminal attack, theft of paperwork or data storage device for 7% and actions taken by a rogue employee or insider threat for 6%.
Cyber incident breaches
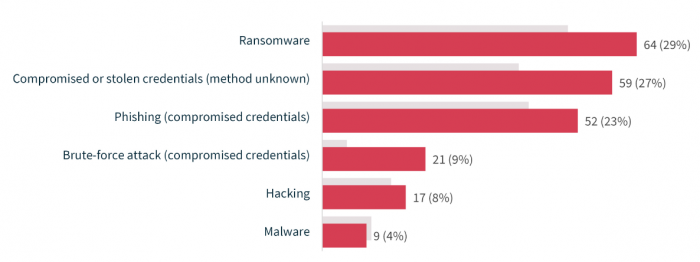
The top sources of cyber incidents were ransomware (29% of cyber incidents; 64 notifications), compromised or stolen credentials (method unknown) (27%; 59 notifications) and phishing (23%; 52 notifications).
To gain initial access to an entity’s networks or systems, threat actors commonly use compromised or stolen credentials. This reporting period, 59% of cyber incidents involved malicious actors exploiting compromised or stolen credentials, including phishing, brute-force attacks, and cases where the method was unknown. If compromised credentials are used by a threat actor, and this is not prevented or promptly detected, this can lead to further kinds of data breach incidents, including ransomware attacks.
Other sources of cyber incidents were hacking (8% of cyber incidents; 17 notifications) and malware (4% of cyber incidents; 9 notifications).
Key takeaways
If your organisation is covered by the Privacy Act 1988 it must notify individuals who have been affected by a data breach, as well as notifying the OAIC when a data breach is likely to result in serious harm to an individual. Malicious or criminal cyber-attacks such as ransomware, phishing and the use of compromised credentials remain the leading source of breaches.



